Our products feature an expansive set of cyber hardened features, built from the ground up to support the most stringent cyber requirements. Our Cyber Secure products include many (or all) of the elements from the following categories:
Physical Protection

- All enclosure access doors include hasps for installation of a locking device to physically prevent access to the internal components of the enclosure
- All panels include an internally-mounted intrusion detector to sense when the panel enclosure is opened. The intrusion events are indicated on all system user interfaces (as warning events) and stored in the log file
- Any unused communication ports are disabled or rendered in accessible
- Configuration data will be stored in memory that is soldered to the control board or physically protected from removal from the control board using a soldered connection
Access Control
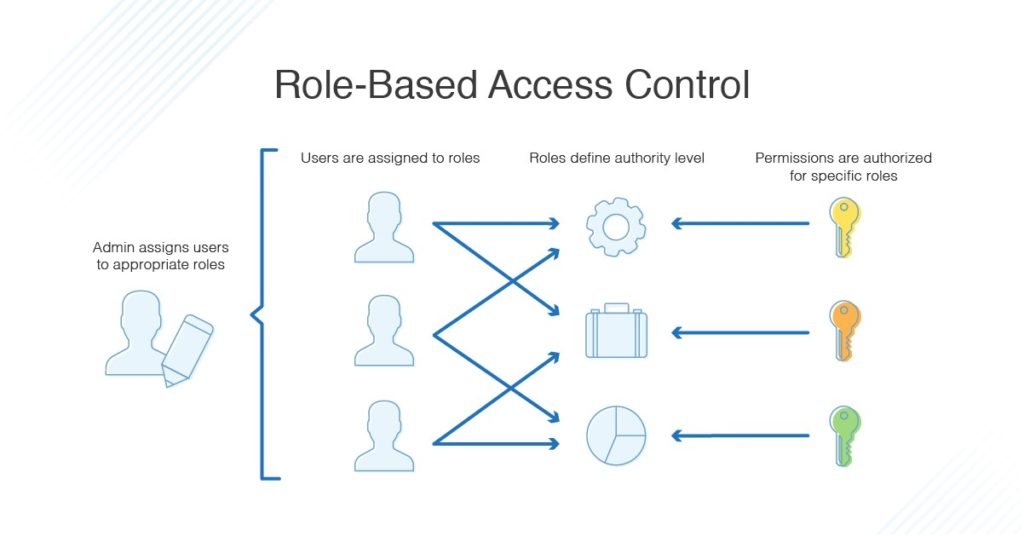
- All panels support Role Base Authentication Control (RBAC). RBAC allows the creation of rights (specific features to regulate), roles (collection of rights), and users (with assigned roles) to control access.
- The configuration software will set all communication ports to disabled by default
- Configuration parameters can only be changed using the configuration software and the configuration port
- All Configuration data / parameters will be checked to ensure they are within acceptable ranges prior to loading the configuration
- Configuration will be stored in a data file that requires elevation of an operator with the Configuration Role for write access
- The configuration port will not auto-execute software or firmware beyond that which is necessary to complete the connection to the configuration tool
- The configuration port will use encrypted communications when interfacing with the configuration tool
- Provide portable ‘program-only’ configuration tools that can run on a variety of platforms (including Linux), does not need to be installed, and can run from a read-only device such as a read-only DVD
- Access Control Lists: List that will allow or reject traffic from specified set of addresses (MAC and IP).
Identification and Authentication
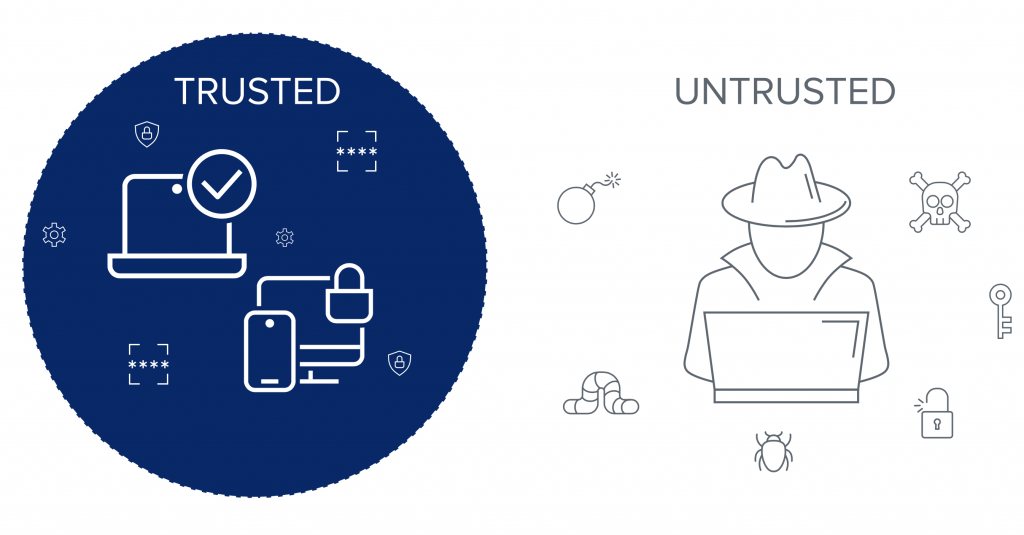
Implement “Trust Group” to ensure that only certified components (hardware and software) are operating the system. If components are introduced that are not certified then systems can alert operators. Trust Group concepts include:
- Components are assigned to trust groups with associated Credentials
- Components must belong to the same trust group to inter-operate (Credentials authenticated)
- Only trusted hardware items can be used
- Only trusted software (firmware and User program) can be installed
- Multi-factor Authentication for Configuration
- Must possess original configuration files (with keys)
- Must know the password for user with Configuration Rights
- Summary: All panels include FIPS compliant mechanisms that can validate network attached panels and third party devices (machinery control systems, remote interfaces, configuration laptops, etc) are trusted members
System Integrity
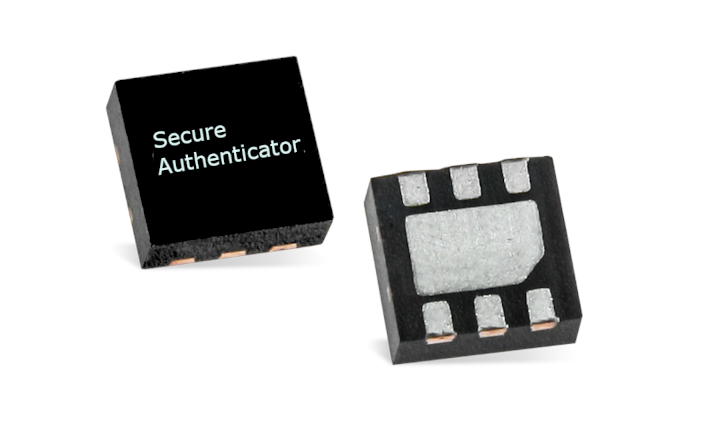
- Includes a ‘Secure Authenticator’ integrated circuit used for secure storage and processing of system and device cryptographic keys
- The processor includes a protected secure enclave that performs a trusted boot which verifies the firmware and boots in a known secure state
- Whitelisting: The host operating system only allows specific / pre-defined processes to run
- Software/Firmware and Configuration Files are validated for software authenticity (i.e., software is from Fairmount Automation and/or from a specific project), integrity (i.e., has not been modified), and confidentiality (i.e., encrypted to protect contents)
- The panels may be restored to a known, trusted state that validates authenticity, integrity, and confidentiality. Only authenticated users with configuration rights are permitted to initiate the restoration process. Initiation of the restoration process will be stored in the log file.
- All panels include mechanisms to wipe system and configuration data
- Configuration files at rest (configuration PC, embedded target, flash drives, etc) are stored in an encrypted state. Data at rest shall be cryptographically protected in accordance with the Federal Information Processing Standard (FIPS) 140-2 Advanced Encryption Standard (AES) at key strength of 256 bits minimum.
Communication Protection
- Incorporates encrypted messaging throughout the product using keys from Trust Group
- Wireless networking capabilities can be prohibited and disabled.
- Mechanisms that provide a Digital Signature of messages:
- Authenticity: verifies message source
- Integrity: data was not altered
Audit & Historical Evidence

- All user actions and important system activity, including maintenance actions and system faults (with state), are logged and stored in a non-volatile system log file. The device will report a fault if anomalies are detected
- Logging system can forward logs to a remote System Log (SysLog) Server.
- Provide a hash of the firmware image and all user configuration files on request
